IMPORTANT – THIS PROCESS IS MANDATORY TO SUPPORT TLS 1.2 WITHOUT IT CELIVEO WON’T WORK
According to PCI Security Standards Council, 30 June 2018 is the cutoff date for disabling SSL /early TLS protocols and implementing a more secure encryption protocol – TLS 1.1 or higher (TLS 1.2 is strongly recommended) in order to meet the PCI Data Security Standard (PCI DSS) for secure communication.
Microsoft has released several patches both for Server side (SQL Server) and client side (Machine connecting to SQL Server) to enable TLS 1.2 support.
All the information can be found in the following link: https://support.microsoft.com/en-us/help/3135244/tls-1-2-support-for-microsoft-sql-server
Process for disabling SSL/ Early TLS protocols and re-configuring CSS/ SSS settings:
1. Update Windows OS:
Make sure that your Windows Server is up to date. Microsoft’s latest update provides support for TLS System Default Versions. The Windows Update (mentioned below) enables the use of TLS v1.2 in .NET Framework 3.5 and its higher versions.
To download patch file for:
Windows Server 2012 R2: https://support.microsoft.com/en-us/help/3154520/support-for-tls-system-default-versions-included-in-the-net-framework
Windows Server 2012: https://support.microsoft.com/en-us/help/3154519/support-for-tls-system-default-versions-included-in-the-net-framework
Windows Server 2008 R2: https://support.microsoft.com/en-us/help/3154518/support-for-tls-system-default-versions-included-in-the-net-framework
Windows Server 2016: The following two Microsoft patches are mandatory for TLS 1.2 to be active on Windows Server 2016. The latest versions currently available are as of 2019-07.
- KB4509091 – Servicing Stack Update for Windows Server 2016 for x64-based Systems (SSU) – https://www.catalog.update.microsoft.com/Search.aspx?q=KB4509091
- KB4507460 – Cumulative Update for Windows Server 2016 for x64-based Systems – https://www.catalog.update.microsoft.com/Search.aspx?q=KB4507460
Notes:
- Make sure to restart the system, after installing the patch file.
- If your system is already up to date via Windows Update, then proceed to the next step.
2. Update SQL Server:
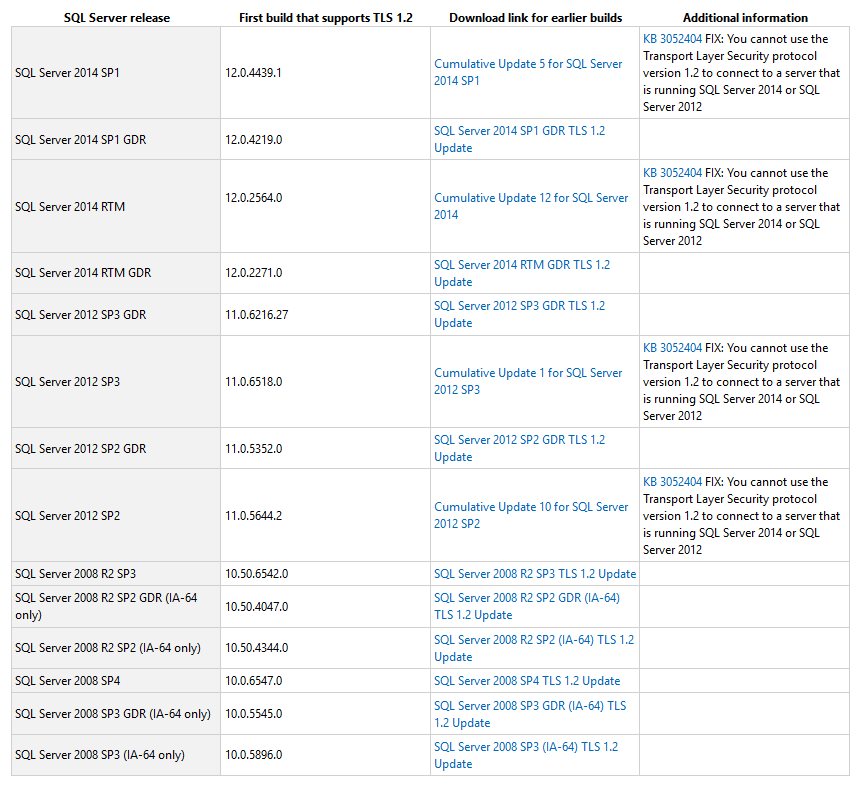
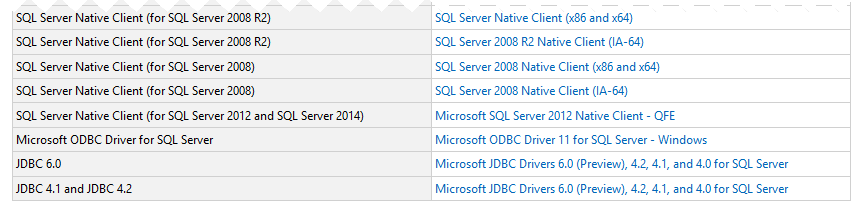
- Refer to the table given in the link https://support.microsoft.com/en-us/help/3135244/tls-1-2-support-for-microsoft-sql-server to download the correct SQL Server patch.
- Apply the SQL Server patch accordingly to your version (Latest SQL Server might not require this step).
3. Enable/Disable SSL/TLS protocols:
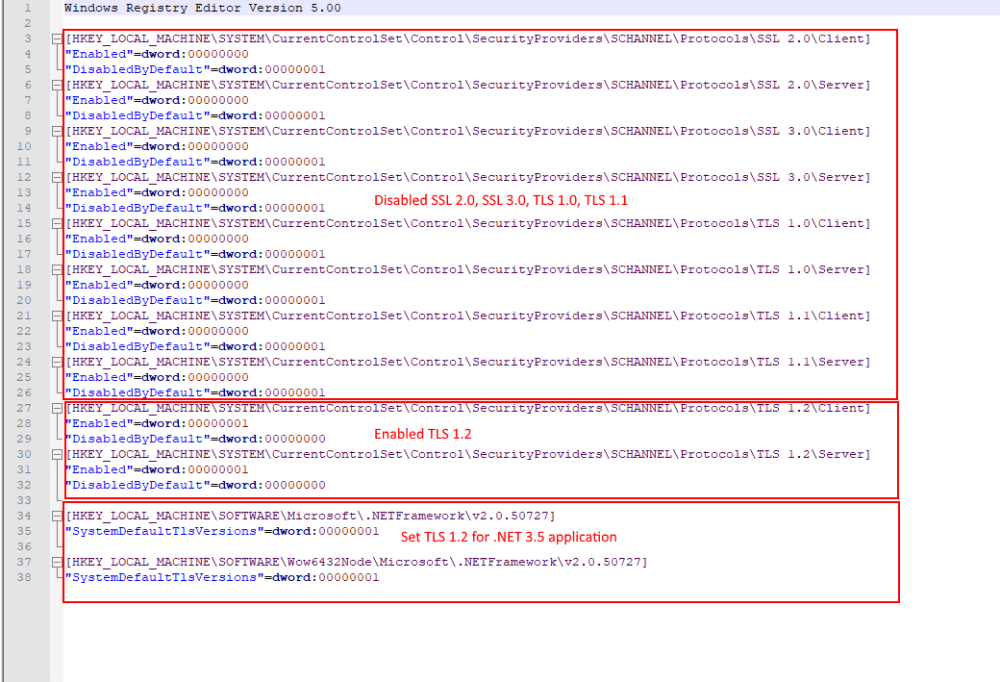
- You can manually disable SSL 1.0/2.0/3.0 and early TLS protocols and enable TLS 1.2 in the Registry. Refer to the document available here on how to do this.
- Alternatively, you can download and run the TLS RegistryEdit script file to update the registry on application and database server.
- Make sure the registry keys are set as shown below:
Notes:
- At this point RDP to connect to the remote server might stop working in some cases because TLS 1.0 will be disabled. Make sure that you are using the latest RDP/windows update.
- Some of the settings on Registry (HKLMSYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols) may also change. So a registry backup or VM Snapshot is recommended.
4. On the Server Running CSS:
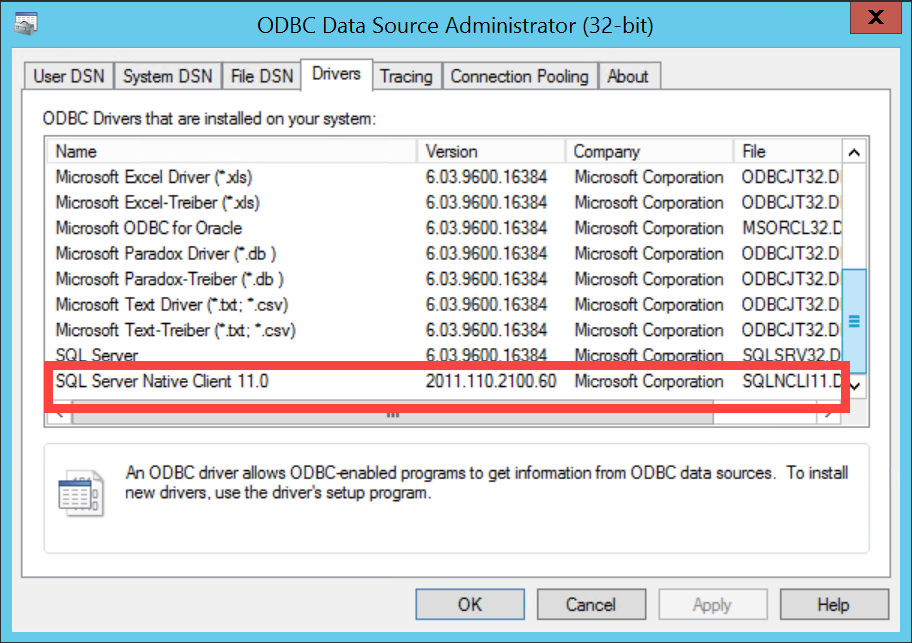
- Apply the SQL Server Native Client patch corresponding to the SQL Server that it will connect to.
You can download the patch from here: https://support.microsoft.com/en-us/help/3135244/tls-1-2-support-for-microsoft-sql-server
- Verify that SQL Server Native Client 10 or higher is installed on the server or client machine running CSS/ SSS (Serverless/ Server-based).
On the machine:
- Now, Launch the CSS/ SSS Configuration tool as Administrator.
- Go to the Roam Printing tab.
- Change the Connection string in order to force the SQL native client provider instead of the OLEDB:
Provider=< Name of the file without the extension >;Data Source=< Server IP Address_or_Host name >;Encrypt=True;TrustServerCertificate=True;
For example: Provider=SQLNCLI11; Data Source=192.168.13.202; Encrypt=True; TrustServerCertificate=True;
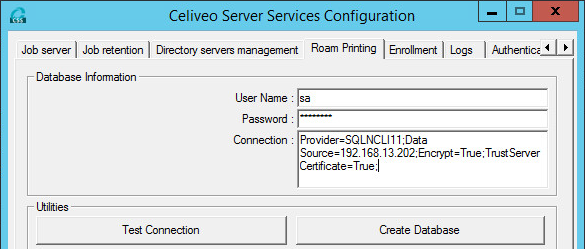
- Apply the same configuration on Enrollment tab.
- Press OK/Apply.
Alternatively, the Connection string can also be configured via Celiveo Web Admin application.
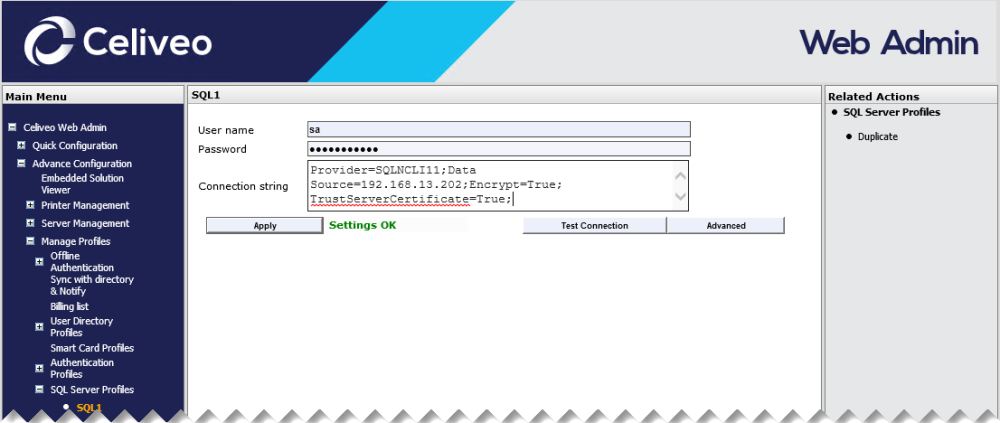
- Once the patch is applied on the SQL Server and TLS 1.1/1.2 is enforced, SQL Management studio won’t be able to access the SQL DB as it also requires a patch or a newer version.
- RDP might require an update for Admins to login on the SQL Server since it normally operates on SSL.
- Other 3rd party software might not work as expected since SSL 1.0/2.0/3.0 and TLS 1.0 is forcibly disabled on the SQL Server machine.



Post your comment on this topic.